What is STIR/SHAKEN?
STIR/SHAKEN is a set of protocols designed to combat caller ID spoofing, a technique used by scammers to mask their real phone number with a fake one. SHAKEN and STIR work together to check the authenticity of a call’s origin and ensure that the caller ID name information matches the actual caller. In the United States, the Federal Communications Commission (FCC) requires most IP-based voice service providers to implement STIR/SHAKEN under its rules for mitigating robocalls.
STIR
STIR (Secure Telephony Identity Revisited) is a set of technical STIR/SHAKEN protocols designed to combat caller ID spoofing. It helps to verify and authenticate the calling party’s identification by using digital certificates to sign calls with a unique identifier. It operates at the network level, using digital signatures in SIP signaling, to support features such as verified caller indicators on end devices. It employs a standardized process for verifying the identity of callers.
SHAKEN
SHAKEN (Signature-based Handling of Asserted information using toKENs) provides standards for how service providers manage STIR-authenticated calls. It outlines and defines how service providers implement Secure Telephony Identity Revisited technology to authenticate calls made or received over the IP network, using a hierarchical framework of digital certificates to verify the authenticity of calls. This provides an end-to-end solution for verifying caller identity.
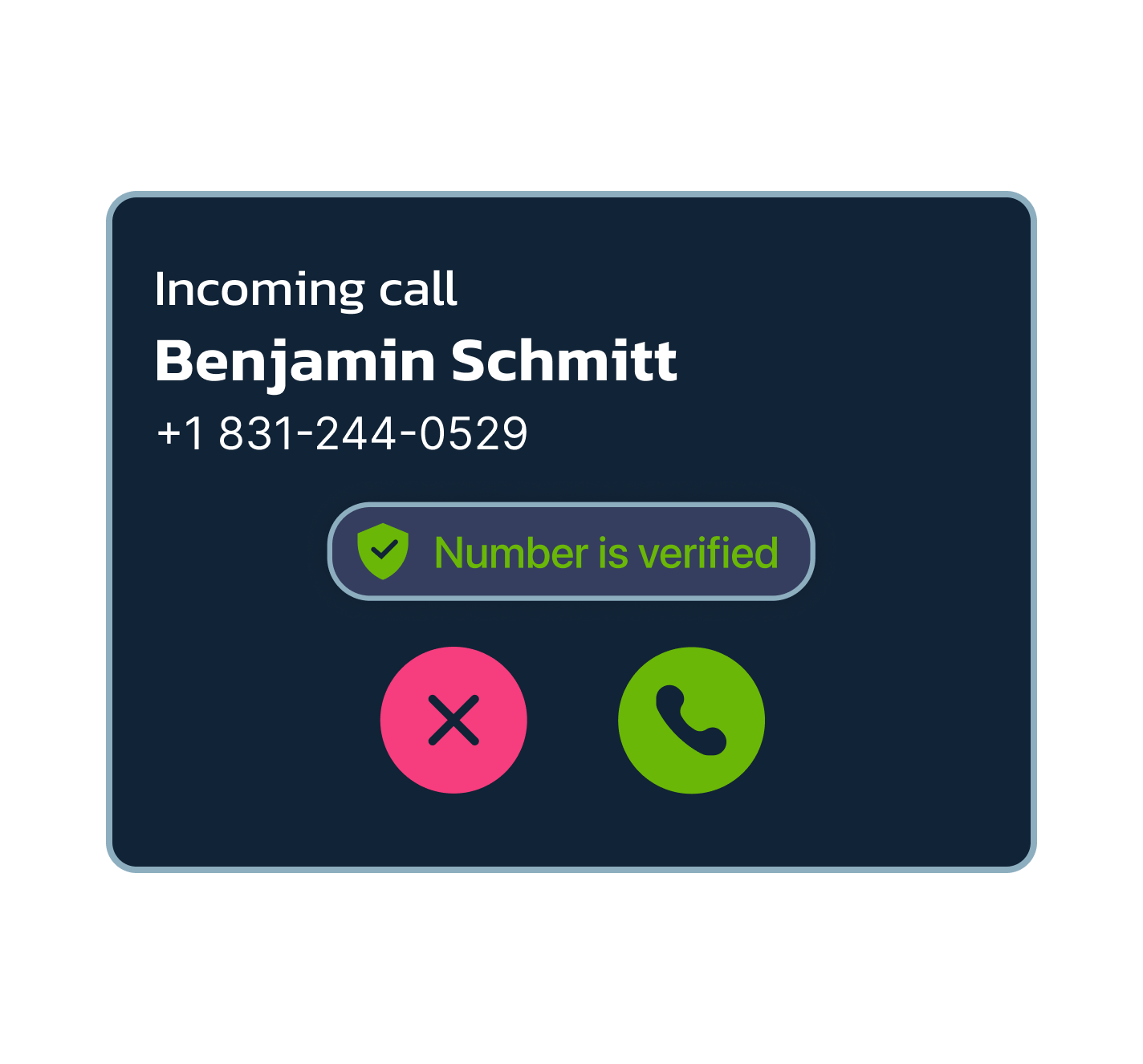
What does the STIR/SHAKEN feature look like?
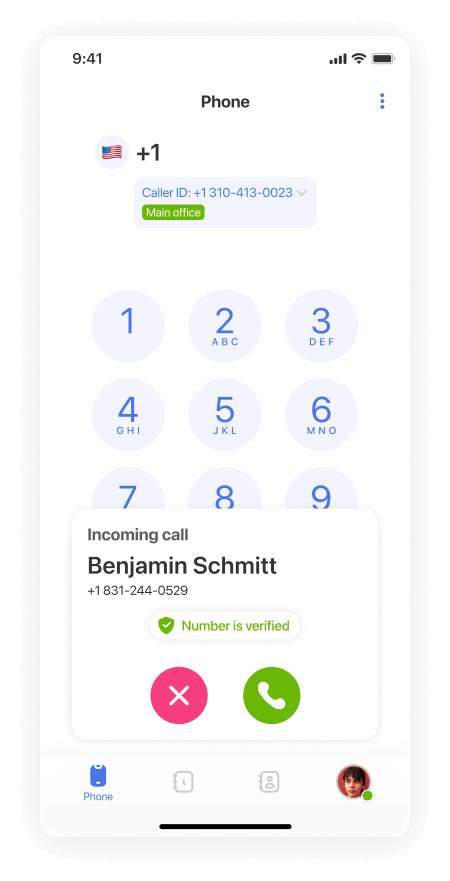
Users can access SHAKEN/STIR settings through a dedicated tab or menu within their telephone system interface. This tab includes options to turn the feature on or off. Additionally, MightyCall provides users with a real-time call status icon right next to the call, so you will know if the call is identified as potentially fraudulent, allowing you to take appropriate action.
Why is the STIR/SHAKEN framework so important?
It protects businesses from spam calls
By doing incoming call authentication and assigning attestation levels on the likelihood that the call is legitimate, the system can help identify and block unwanted spam calls before they reach the recipient’s telephone. This can save users time and frustration, and help reduce the overall volume of spam calls in circulation.
It is an effective measure against robocalls
Robocalls are automated calls that often contain pre-recorded messages and are a common tactic used by scammers and spammers. By identifying these calls as potentially fraudulent and assigning them a low verification result, the system can help to prevent them from reaching users’ phones, reducing the annoyance and risk associated with spam calls.
It allows businesses to protect their reputation
The STIR/SHAKEN framework can help to protect the reputation of legitimate businesses and service providers. By checking the authenticity of their calls and assigning them a high attestation outcome, the system can help to ensure that these calls are not mistaken for spam or fraudulent calls. This helps build trust with customers and prevent unnecessary disruptions to legitimate business operations.
schedule your personalized demo with our amazing team

How does STIR/SHAKEN work?
- When an incoming call is received, the system checks the caller identity information associated with the call.
- The system then uses cryptographic STIR/SHAKEN certificates to check the authenticity of the caller identity information and ensure that it has not been tampered with.
- Based on this verification process, the system assigns a verification result to the call, indicating the likelihood that it is a legitimate call.
- This outcome is then passed along with the call to the recipient’s telephone system, where it can be used to determine how the call should be handled.
- If the attestation outcome is high, indicating a high likelihood that the call is legitimate, the call is allowed through to the recipient’s phone.
- If it is low, indicating a high probability that the call is spam or fraudulent, the call may be blocked or flagged for further review by the recipient’s telephone system.
STIR/SHAKEN attestation levels
The framework uses a process called attestation to check the authenticity of incoming calls. There are three different attestation levels, each with its own requirements and implications. Here’s a brief overview:
- Full Attestation: This attestation level requires the caller’s identity to be checked using cryptographic certificates, ensuring that the call originates from a trusted source.
- Partial Attestation: This level is used when the call’s identity cannot be fully verified, but the system can confirm that the call originates from a specific service provider.
- Gateway Attestation: This STIR/SHAKEN attestation level is used when the call originates from a foreign service provider that does not support the technology. In this case, the gateway provider marks the call with a ‘gateway attestation,’ indicating it originated outside a verified network but was received through a known entry point.
By verifying the authenticity of incoming calls using this system, MightyCall can help to reduce the volume of spam and fraudulent calls that users receive, improving the overall quality of their telephone experience.
STIR/SHAKEN call flow
When the STIR/SHAKEN call technology is used, the call flow involves several key steps:
- The originating service provider generates a SIP INVITE message to initiate the call, including the caller’s phone number and identity information.
- The originating provider signs the message using a private key and includes the signature in the message.
- The originating provider signs the call with its digital certificate; intermediate carriers usually forward the signed data unchanged. The terminating provider then verifies the signature using the originating provider’s public certificate.
- The final provider verifies the signatures on the message using public keys provided by the originating and intermediate service providers.
- Based on the results, the final provider generates an attestation outcome, indicating the likelihood that the call is legitimate.
- Then, it is passed along with the call to the recipient’s telephone system, which can use it to determine how the call should be handled.
How to achieve verified calls?
From the user side
Make sure that you are using a phone system or app that supports the STIR/SHAKEN deployment. Contact your service provider to confirm that they are implementing STIR/SHAKEN and to ensure that your account is set up correctly to receive verified calls.
From the service provider side
Implement the framework on your telephone system to provide safe services for your customers. Collaborate with other service providers to ensure that call signatures are properly authenticated and verified throughout the call flow, allowing for accurate verification results.
What is MightyCall doing for STIR/SHAKEN compliance?
- We began working on STIR/SHAKEN compliance in early 2021, in response to the growing problem of spam and fraudulent calls.
- We have implemented the necessary technical changes to ensure that our telephone system can properly authenticate and handle calls using the structural framework.
- We have added a new “Verification Status” icon on the incoming calls. This allows users to easily identify and filter verified calls from those that did not pass the test.
- We continue to monitor industry developments and best practices related to this security technology. We will continually update and improve our platform as needed to maintain compliance and deliver the best possible user experience.
STIR/SHAKEN features in MightyCall
MightyCall features several internal functions designed to enhance the security and reliability of our users’ telephone systems. Here are a few examples:
- Caller Identification (ID) authentication: Verifies incoming calls and displays a “verified” status in the call logs if the call passes the test.
- Call blocking: Allows users to block calls from specific phone numbers or area codes, reducing the volume of unwanted calls.
- Fraud detection: Uses machine learning to identify potential fraud or spam calls and alerts users to the possible danger.
- Number authentication: Verifies the authenticity of outgoing calls to improve the reputation of legitimate businesses and service providers and reduce the risk of fraud.
How to configure and customize caller ID authentication in MightyCall
Enable or disable displaying caller ID
- Log in to your MightyCall account and navigate to the “Settings” tab.
- Select “Caller ID Authentication” from the list of options.
- Under “Authentication Settings”, choose whether you want to enable or disable the feature.
Customize call log display settings
Under “Call Log Display Settings”, select which columns you want to include in your call logs.
Add numbers to the blocklist
Under “Blocklist Settings”, add any phone numbers or area codes that you want to block from your telephone system.
Enable or disable fraud detection
Under “Fraud Detection Settings”, choose whether you want to enable or disable the Fraud Detection feature. If enabled, the system will analyze call patterns and identify potential fraud or spam calls, flagging them for your review.
STIR/SHAKEN call authentication on Android and iOS
If you want to have every MightyCall feature in your pocket, download our free Mobile App for iOS or Android today. You will stay on top of things at all times.
Why use STIR/SHAKEN technology?
Reduce the volume of unwanted calls
By verifying the authenticity of incoming calls and attaching a verification status based on their likelihood of being legitimate, the system helps filter out spam and fraudulent calls, allowing users to focus on the calls that matter.
Improve call quality and reliability
By ensuring that incoming calls are properly authenticated and verified, the system can help to reduce the risk of fraud and improve the accuracy of call routing, leading to a better overall user experience.
Enhance reputation protection
For businesses, using STIR/SHAKEN apps can be particularly important in terms of reputation protection. By verifying the authenticity of outgoing calls and ensuring that caller identity information is accurate and trusted, businesses can build a stronger reputation and reduce the risk of fraud or spam accusations.
Stay compliant with regulations
In many cases, compliance may be required by industry regulations or government agencies. By implementing this feature, users and businesses can ensure they meet these requirements and avoid potential penalties or fines.
Protect sensitive information
For users and businesses that handle sensitive information, STIR/SHAKEN standards can provide an additional layer of protection against unauthorized access or fraudulent attempts. By verifying the authenticity of incoming calls, the system can help to reduce the risk of social engineering attacks and other types of fraud that rely on spoofed caller identity information.
Build trust with customers
Build trust with customers and partners by demonstrating your commitment to security and reliability. By providing a telephone system that is resistant to fraud and spam, businesses can enhance their reputation and build stronger relationships with key stakeholders.
Use case
Jane, the owner of a small business, faced an issue of receiving spam and fraudulent calls. She implemented the caller ID authentication solution to improve security and reliability. It reduced the volume of unwanted calls and spam, filtering out unwanted calls with the “Verification Status” icon. Jane built trust with customers and partners by ensuring that outgoing calls were authenticated and trusted.
Helpful terms to know about STIR/SHAKEN
- Attestation: Attestation refers to the process of verifying the authenticity of an incoming or outgoing call. This is typically done by attaching a verification status to the call, based on factors such as the caller’s identity information and the reputation of the originating phone number.
- Call validation status: The call validation status refers to the result of the verification process for a specific call. This status can be “Pass”, “Fail”, or “Partial”, depending on the outcome of the verification test.
- Robocall mitigation: Refers to the measures taken to reduce the volume of robocalls that users receive. This security tactic is one example of a robocall mitigation technique, as it helps filter out spam and fraudulent calls based on their likelihood of being legitimate.
- Call blocking: Call blocking is a feature that allows users to block specific phone numbers or types of calls from reaching their telephone system. This can be an effective way to reduce the volume of unwanted calls and spam that users receive.
Is STIR/SHAKEN required by law?
United States
In the United States, the TRACED Act was passed in 2019, which mandates the implementation (specifically for IP-based voice networks, with alternative robocall mitigation requirements for others) of this security tactic for all telephone service providers. The law requires that providers implement a robocall mitigation program that includes the use of this safety measure tactic and provides penalties for noncompliance. The Federal Communications Commission (FCC) is responsible for overseeing and enforcing compliance with the law.
Canada
In Canada, the Canadian Radio-television and Telecommunications Commission (CRTC) has implemented regulations requiring telecommunications service providers to use this security technology. The regulations aim to reduce the number of nuisance calls and improve call transparency and accountability. You can find more information about the CRTC’s regulations on the use of this security tactic on their website.
Other countries
While this security measure is currently being implemented in the United States and Canada, other countries may also adopt the technology in the future as part of their efforts to combat robocalls and improve call transparency. However, the use of this security tech may vary depending on local regulations and infrastructure.
How businesses can prepare for STIR/SHAKEN implementation?
- Verify your caller identity information: Ensure that your caller identity information is accurate and up-to-date, as this will be used to authenticate your outgoing calls. If it’s incorrect, update it with your service provider.
- Review your call handling processes: Take a close look at how your business handles incoming and outgoing calls, and make sure that your processes align with these security tactic requirements. This may involve changes to call routing, call screening, or other call handling procedures.
- Educate your team: Inform your team members about the benefits and requirements of implementing this security method, as well as any necessary changes to call handling processes. This will ensure that everyone is aligned and working towards a common goal.
- Choose a reliable STIR/SHAKEN solution: Select a reputable provider that can offer the necessary support and resources for successful implementation. Ensure the provider aligns with your business needs and objectives.
Ready to start using STIR/SHAKEN technology?
While many different programs provide STIR/SHAKEN services, MightyCall offers a superior solution with a range of advantages. With a large number of internal settings and an easy-to-use interface, our program makes it simple for businesses to implement and benefit from the technology. Whether you’re looking to reduce the volume of unwanted calls or build trust with your customers and partners, MightyCall can help you achieve your goals.